Cyber Threat Intelligence identifies cyber threats that are aimed at any particular business. IT specialists and complex tools can read and analyze the threats.
What is cyber threat intelligence?
Cyber threats aimed at business are identified by Threat Intelligence. Therefore IT specialists and complex tools can read and analyze the threats. This information helps to plan, forestall, and recognize cyber threats. Hoping to exploit important organization’s assets.
Eventually threat Intelligence collects and compiles the raw data about the threats emerging from different sources.
Cyber threats can be truly terrifying. Cyber threat knowledge can help associations obtain important information about these threats, build successful defense equipment and relieve the threats that could harm their reputation.
People often confuse between Cyber Security terms such as Threat Intelligence and Threat Data. Threat data is a list of likely threats. Furthermore, For instance, Facebook feeds are like a running list of possible issues. It is Threat Intelligence when IT specialists and exclusive complex tools can read and analyze the threats/attacks.
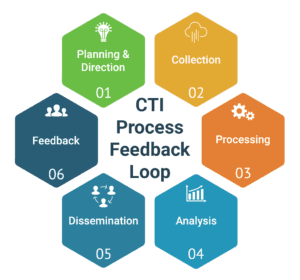
Why is threat intelligence important for businesses?
Threat Intelligence is a vital part of any cybersecurity. A cyber threat intelligence program sometimes called CTI, can:
Prevent data loss
With a very much organized CTI program set up, your organization can spot cyber threats hence keep data breaches from leaking critical information.
Give guidance on security measures
By distinguishing and dissecting threats, CTI spots designs utilized by hackers. CTI assists organizations with setting up security standards to protect against future cyber assaults and threats.
Educate others
Hackers are smarter than before. Besides, To keep up, cybersecurity specialists share the strategies they’ve seen with the IT people group to make a communal database to battle cybercrimes and cybersecurity threats.
